How Secure is Cryptocurrency and Blockchain
Just How Secure is Cryptocurrency and Blockchain?
As an author and Virtual Capital Ventures partner William Mougayar has pointed out, the old question “is it in the database?” could soon be replaced by “is it in the blockchain?”
Blockchain has moved on from its bitcoin origins and is making inroads into non-fiscal applications, including direct cyber security. Technology providers and early adopters, as well as the growing army of cryptocurrency investors, have put the spotlight on this distributed security technology.
But just how secure is Blockchain and the cryptocurrencies that depend on it?
In this article I want to look at the technology and its uses, as well as some of the ways that cryptocurrencies have been stolen. Finally, we will also look at some of those aforementioned non-fiscal applications to get a measure of blockchain’s security away from cryptocurrency.
What is Blockchain?
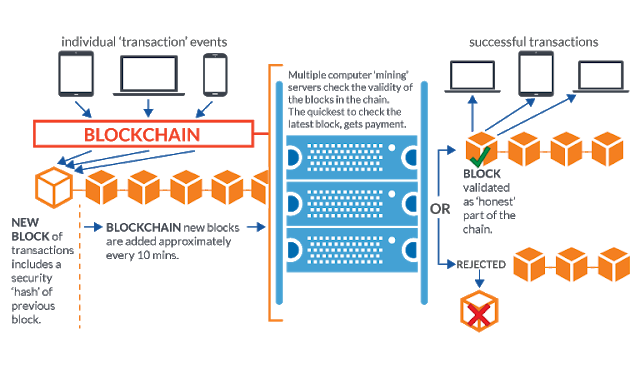
Satoshi Nakamoto devised blockchain in 2008 in order to support bitcoin, the first cryptocurrency. The key business problem was to prevent a currency holder from spending their cash more than once. The technology he envisaged would allow the community to supervise transactions. Once approved, a sequence of unique transactions would be frozen in a block and subsequent blocks would link back to it, forming a secure chain (hence the term ‘blockchain’ was born).
Blockchain is a replicated database then, which allows consensus on transactions without reliance on a central server. Being both distributed and decentralised means it can continue to function if one of the nodes fails, making it robust in the face of tampering, security vulnerabilities or coordinated cyber attacks.
Blockchain is now being used to record transactions far beyond its original purpose. For example, the Swedish land registry authority has been testing the use of blockchain for recording property transactions; the perceived benefit being to make the process more efficient, particularly to eliminate paperwork while improving security.
Cryptocurrency Hacks

Despite being underpinned by Blockchain, cryptocurrencies like Bitcoin aren’t invulnerable to hacks and theft. Below are some examples of high profile cases.
Coincheck Hack
In January this year, $500M was stolen from the Japanese cryptocurrency exchange service Coincheck. It was later reported that cryptocurrency “coins” had been stored in a “hot” wallet. Whereas most exchanges hold funds offline, Coincheck had opted against doing so, which is a very basic security precaution. The theft was carried out by the acquisition of a user’s private key, resulting in calls for greater use of multi-signature (multisig) transactions. However even multisig is prone to manipulation as Bitfinex found when it lost $65M in 2016.
NiceHash Hack
In December 2017, Slovenian-based crypto-mining marketplace, NiceHash, was hacked and more than $60M was stolen from the NiceHash bitcoin wallet. In the attack, the stolen coins were moved to an external wallet. No clear explanation for the theft has been reported; consensus on the forums is that this was an inside job and blames incompetence in the company.
Magic: The Gathering Online Exchange (Mt. Gox)
The biggest hack in Bitcoin history took place in 2014 and hit Mt. Gox, the Tokyo-based bitcoin exchange and the largest in the world at the time (the company handled 70% of all bitcoin transactions worldwide). In 2014 the company revealed that 600,000 bitcoins (about 6% of the global supply) had been stolen, a figure worth at the time around $460 million at the time. 200,000 of the coins have since been recovered but the rest remain missing.
A number of reasons have been put forward as to why Mt. Gox was susceptible to attack but it was clear that even basic software development procedures were not implemented. These included:
Multiple developers were working on the code, but there was no version control for the software
There was no prescribed testing policy (or at least not until too late)
Code changes had to be approved by a single signatory (the CEO)
Investigations have found that the company’s huge and rapid growth had caused internal issues, with staff talking of a “disorganized and discordant organization, with poor security procedures.”.
Ethereum DAO Hack
Another eye wateringly huge theft was from Ethereum, an alternative cryptocurrency. Unlike bitcoin, Ethereum is used to run decentralised applications with investors, buying tokens in return for “Ether”, and developers paying for services to fund the platform.
In 2016 a hacker stole around $50M from the fund by exploiting a loophole in the smart contract software, known as Decentralized Autonomous Organization (DAO). The hack involved repeatedly exchanging the same tokens for Ether (before the transaction could be registered).
There has been a lot of commentary on the Ethereum hack and the wisdom of the DAO (which is stateless and therefore not prone to government regulation). Lessons have been learnt but the hack shows the vulnerability of such systems.
Non-fiscal applications
The vulnerability of blockchain is perhaps not of huge concern to those who don’t have large amounts of money tied up in cryptocurrency but when we see it being used for non-fiscal applications, it’s security should be something that concerns all of us.
There are a growing number of non-fiscal applications for blockchain. Guardtime Federal is a leader in the use of blockchain for cybersecurity and last year, Lockheed Martin, the world’s biggest defence contractor, announced a partnership with Guardtime Federal as part of its security approach.
Similarly, Verizon has this year opted to implement Guardtime’s KSI blockchain capabilities.
REMME uses blockchain and sidechain technology to implement a distributed and highly secure database. Clients such as energy suppliers and health information services use its authorisation platform to manage access control while defending against cyber attacks.
These are not cryptocurrency applications but they manage highly sensitive data and critical access control and, as such, need to provide the highest possible resilience to cyber attacks. As citizens who may rely directly or indirectly on these services, we can only hope that these organisations are carrying out due diligence, but also, importantly, in the supplier and its internal procedures.
Is Blockchain Secure?
Whilst the various cryptocurrency hacks are clearly cause for concern, it seems clear that none were caused by systemic faults in the underlying blockchain technology they rely on. Rather it seems that design issues, lack or process, human error and weak senior management have left these blockchain systems open to attack.
There are lessons to be learnt here and if blockchain is to become truly trusted by all of us, then we will need a new generation of cyber security experts to build the protocols and processes that will ensure its proper use.
As Tim Berners-Lee once said “we can’t blame the technology when we make mistakes.”
